Small 75u sample from my first bubble hash attempt. Used a freezer and a microplane. My buddy was in the stars last night so I guess it turned out okay. : BubbleHash

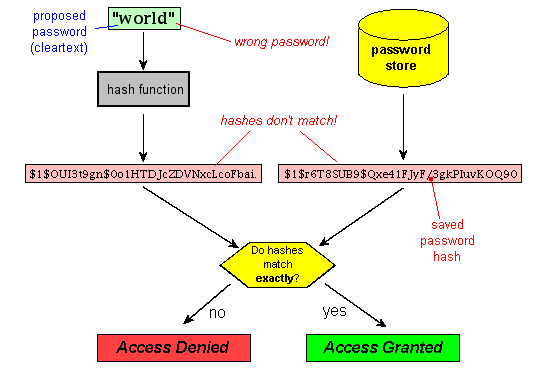
2: A simple depiction of the user authentication process. Evil Eve is... | Download Scientific Diagram
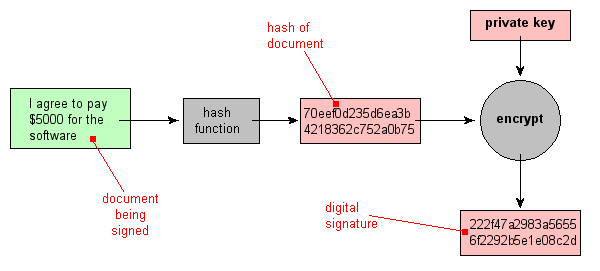
How Cryptographic Hash Functions Solve a Very Difficult and Important Problem | by Bennett Garner | Medium









![What Is Cryptographic Hash? [a Beginner's Guide] What Is Cryptographic Hash? [a Beginner's Guide]](https://techjury.net/wp-content/uploads/2020/06/hash-functions-speed-1024x753.png)